Device Security Schemes¶
To ensure connection security, devices must undergo authentication before accessing EnOS. EnOS supports the following authentication modes:
Secret-Based One-way Authentication: One-way authentication with relatively weaker security, set as the system default.
Certificate-Based Two-way Authentication: Two-way authentication with high security, requiring manual activation by the user.
Authentication Process Overview¶
Regardless of the authentication method, the device authentication process varies by device type as outlined below.
Smart Device Authentication¶
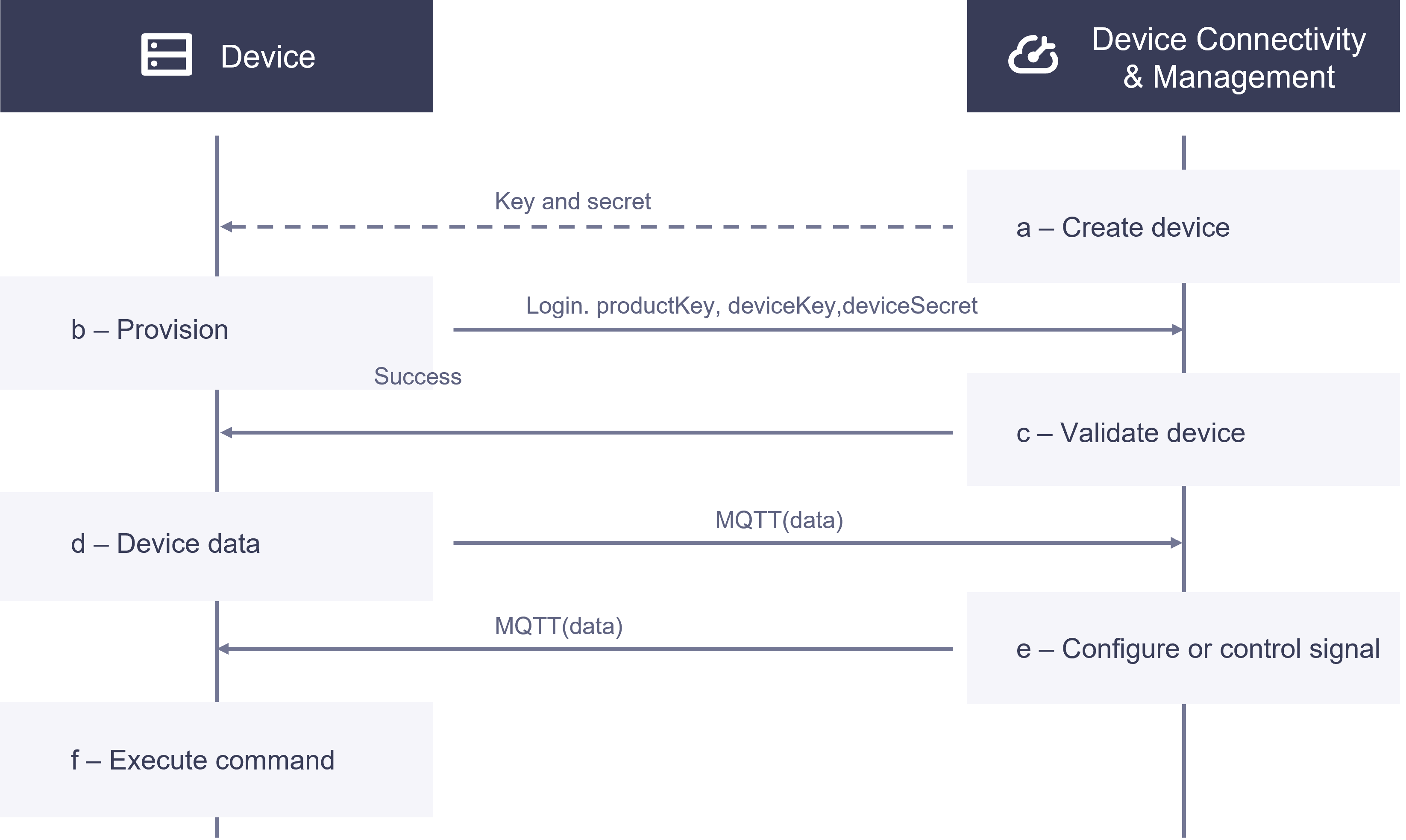
Log in to EnOS Application Portal, access the Developer Console, and create models, products, and register the devices.
Configure the required authentication information on the devices.
Start the devices and attempt to connect to EnOS using the configured authentication information.
If the devices pass authentication, they successfully connects to EnOS; otherwise, the connection fails.
Non-Smart Device Authentication¶
Log in to EnOS Application Portal, access the Developer Console, and create models, products, and register both the devices and their gateway devices.
On the gateway devices, configure the authentication information for the devices needing access.
Start the gateway devices and attempt to connect to EnOS using the configured authentication information.
If the devices pass authentication, they successfully connect to EnOS; otherwise, the connection fails.
Secret-Based One-Way Authentication¶
The secret-based one-way authentication mechanism is the default authentication method in EnOS. More specifically, the default method is the static authentication method within the one-way authentication mechanism. This mechanism uses the following keys:
Product Key and Product Secret
Product Key: A unique identifier issued by EnOS for a product.
Product Secret: A product key issued by EnOS, paired with the Product Key.
For more information, see Viewing Product Information.
Device Key and Device Secret
Device Key: A user-defined or system-generated device identifier during registration, unique within an OU.
Device Secret: A device key issued by EnOS, paired with the Device Key.
For more information, see Retrieving Device Triple Information.
Authentication Process¶
One-way authentication involves the following steps:
Registration
Log in to EnOS Application Portal or use EnOS APIs to register a device instance in the cloud. At this point, the device’s status is Inactive.
To register a device in EnOS Application Portal, you need to sequentially create a model, create a product, and register a device.
Using EnOS APIs, you can create a product and create a device. Creating a model supports in EnOS Application Portal only.
Authentication
Use Dynamic Authentication or Static Authentication to authenticate a registered device. Upon successful authentication, the device status changes from Inactive to Online. If the device does not send any messages to EnOS for a period while Online, its status changes to Offline.
Authentication Methods¶
Devices initially registered in EnOS Cloud are in an Inactive state by default, awaiting authentication. The static authentication methods include:
Dynamic Authentication: The device attempts authentication using product key, product secret, and device key. Upon successful authentication, EnOS returns a device secret to the device. The device uses the triple information for authentication.
Static Authentication: Each device has its triple information (product key, device key, and device secret) pre-programmed. The device attempts authentication with the pre-programmed triple information and completes connection upon success.
Dynamic Authentication¶
To enable dynamic authentication, go to Device Management > Products, select the product requiring dynamic activation, click its View  icon, and access the product details page. On the Product Information tab, toggle the Dynamic Activation switch to ON.
icon, and access the product details page. On the Product Information tab, toggle the Dynamic Activation switch to ON.
The dynamic authentication process is as follows:
A registered but inactive device sends a request containing product key, product secret, and device key to attempt authentication. Upon successful authentication, EnOS returns a device secret to the device for subsequent communication. The device status changes from Inactive to Online. If the device does not upload data for a period, its status changes from Online to Offline.
As long as the device status is Inactive, product key, product secret, and device key can be used repeatedly to obtain the device secret.
For a device that is Online or Offline but requires re-authentication, first delete the device instance in Device Management > Device Assets, recreate the device instance, and then have the device use a new product key, product secret, and device key to obtain a device secret.
After the initial successful authentication, the device will use product key, device key, and device secret for subsequent authentications.
Static Authentication¶
This is the default device authentication method in EnOS. The authentication process is as follows:
The device sends an authentication request to EnOS containing product key, device key, and device secret. These three parameters can be obtained from the Device Management > Device Assets > Device Details page in EnOS Application Portal after you register the device in the cloud. You need to program these parameters on the device.
Upon successful authentication, the device status changes from Inactive to Online. The device can then upload data; if it does not upload data for a period, its status changes to Offline.
Note
For devices that have passed authentication, if anomalies are detected or you no longer wish to receive data from the device, you can disable it on the Device Management > Device Assets page. The device will then go offline and enter a Disabled status.
Certificate-Based Two-Way Authentication¶
EnOS also supports a certificate-based two-way authentication mechanism. In addition to EnOS verifying the trustworthiness of the device, the device also verifies the trustworthiness of the cloud.
When two-way authentication is enabled, EnOS enforces the following security measures to protect connections between devices, gateways, and EnOS Cloud:
Communication between directly connected devices and EnOS Cloud, as well as between gateway devices and EnOS Cloud, must use certificate-based two-way authentication.
Supports signature verification using RSA or ECC algorithms.
Prerequisites¶
To enable certificate-based two-way authentication, log in to the Developer Console in EnOS Application Portal, go to Device Management > Products, and in Product Information, set Certificate-Based Authentication to Enabled.
Best Practices¶
If you enable certificate-based two-way authentication, we recommend the following best practices:
Provide a unique certificate for each device to enable fine-grained management, such as certificate revocation.
Devices support certificate replacement to ensure smooth operation when certificates expire.
Obtaining Certificates¶
The processes for EnOS Cloud and EnOS Edge to obtain an X.509 certificate differ. You can also use gateway devices other than EnOS Edge.
EnOS Cloud Obtaining an X.509 Certificate¶
The figure below shows the process for EnOS Cloud to obtain an X.509 certificate.
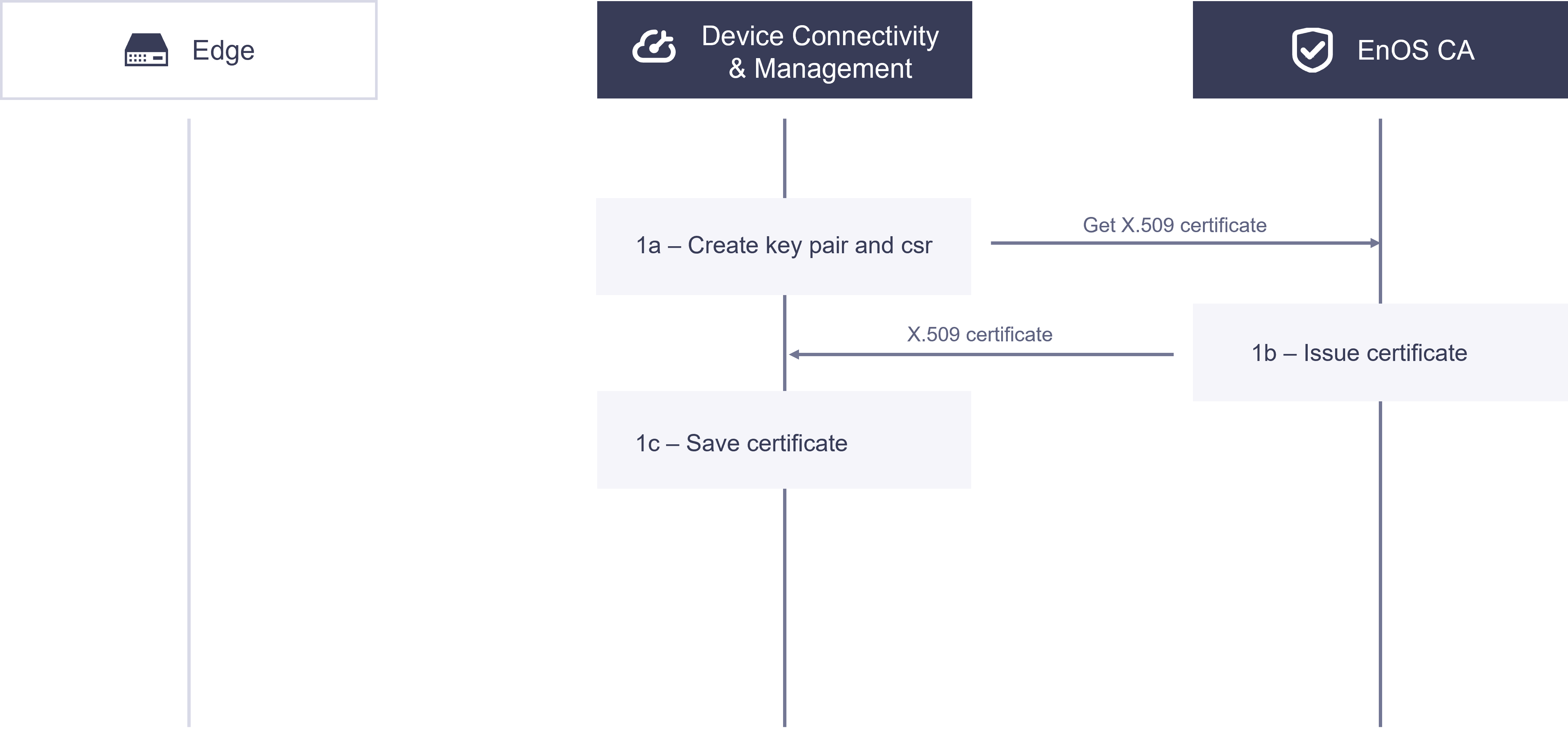
1a. Device Connectivity and Management creates a key pair and Certificate Signing Request (CSR) file locally, using the X.509 Certificate Service API to request an X.509 certificate containing the CSR.
1b. EnOS CA issues the X.509 certificate and sends it to Device Connectivity and Management.
1c. EnOS Cloud receives and stores the X.509 certificate.
EnOS Edge Obtaining an X.509 Certificate¶
The figure below shows the process for EnOS Edge to obtain an X.509 certificate.
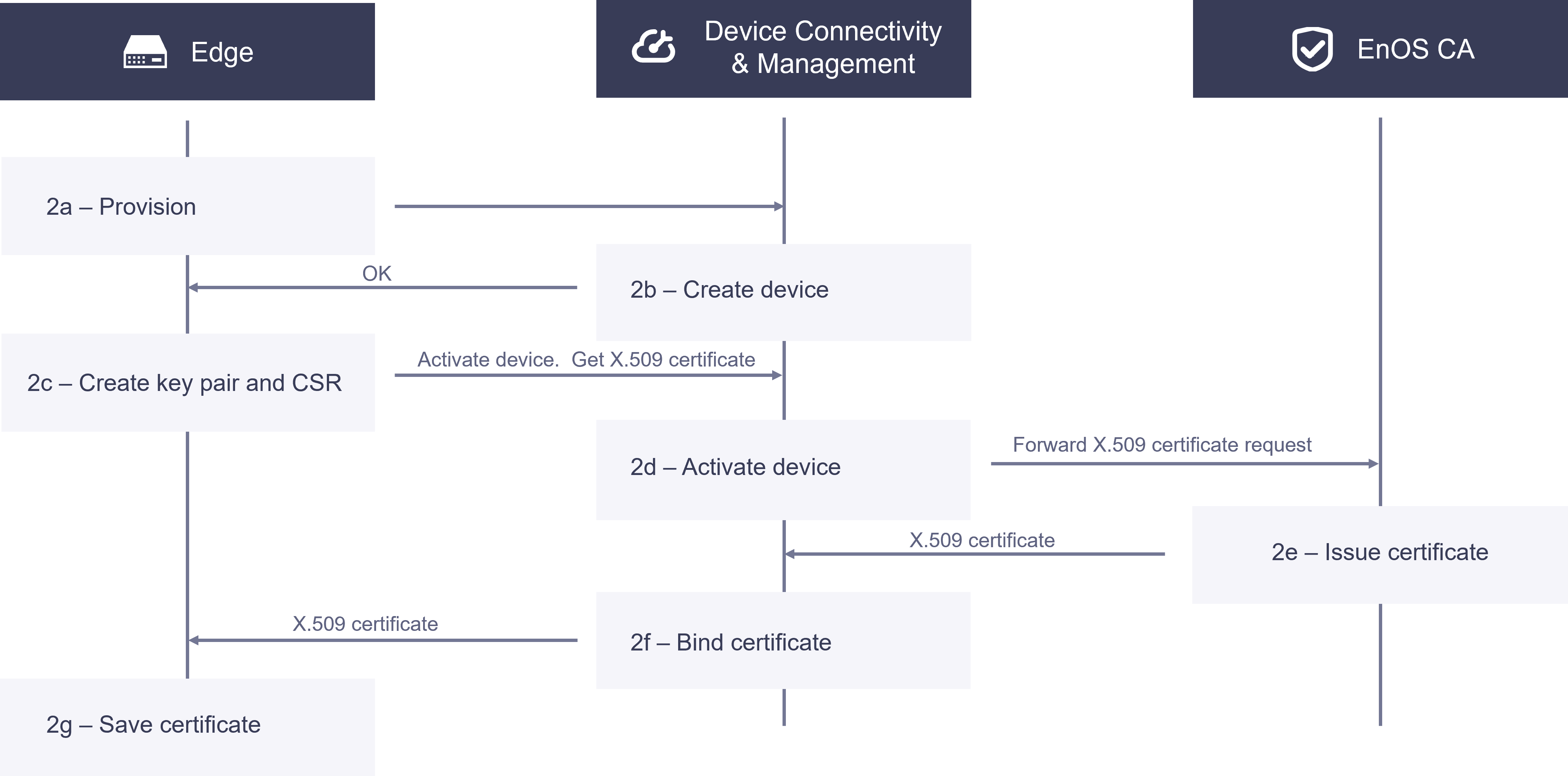
2a. EnOS Edge devices are pre-programmed at the factory with a product key (Product key, product secret) and an EnOS Edge device serial number (SN). After powering on and connecting to the network, EnOS Edge uploads the product key and serial number to the cloud for dynamic activation. If cloud authentication succeeds, a device secret is returned to EnOS Edge.
2b. In Device Connectivity and Management, register the EnOS Edge device using its serial number as the device key. This can be done in the Developer Console of EnOS Application Portal or by calling the Create Device API.
2c. EnOS Edge receives information returned by EnOS Cloud, creates a key pair and CSR file, and calls an API to obtain its X.509 certificate. It simultaneously attempts to log in to EnOS Cloud using the device triple information.
2d. Device Connectivity and Management receives the CSR file from EnOS Edge, verifies its identity, and forwards the CSR file to EnOS CA.
2e. EnOS CA receives the CSR file, issues an EnOS Edge certificate, and sends it to Device Connectivity and Management.
2f. Device Connectivity and Management receives the signed X.509 certificate, binds it to the EnOS Edge device ID, and sends the EnOS Edge certificate to EnOS Edge.
2g. EnOS Edge receives the EnOS Edge certificate and must store it in a secure local repository, such as a Trusted Platform Module (TPM).
Establishing Communication¶
The figure below illustrates the process of establishing certificate-based communication between a device and the cloud:
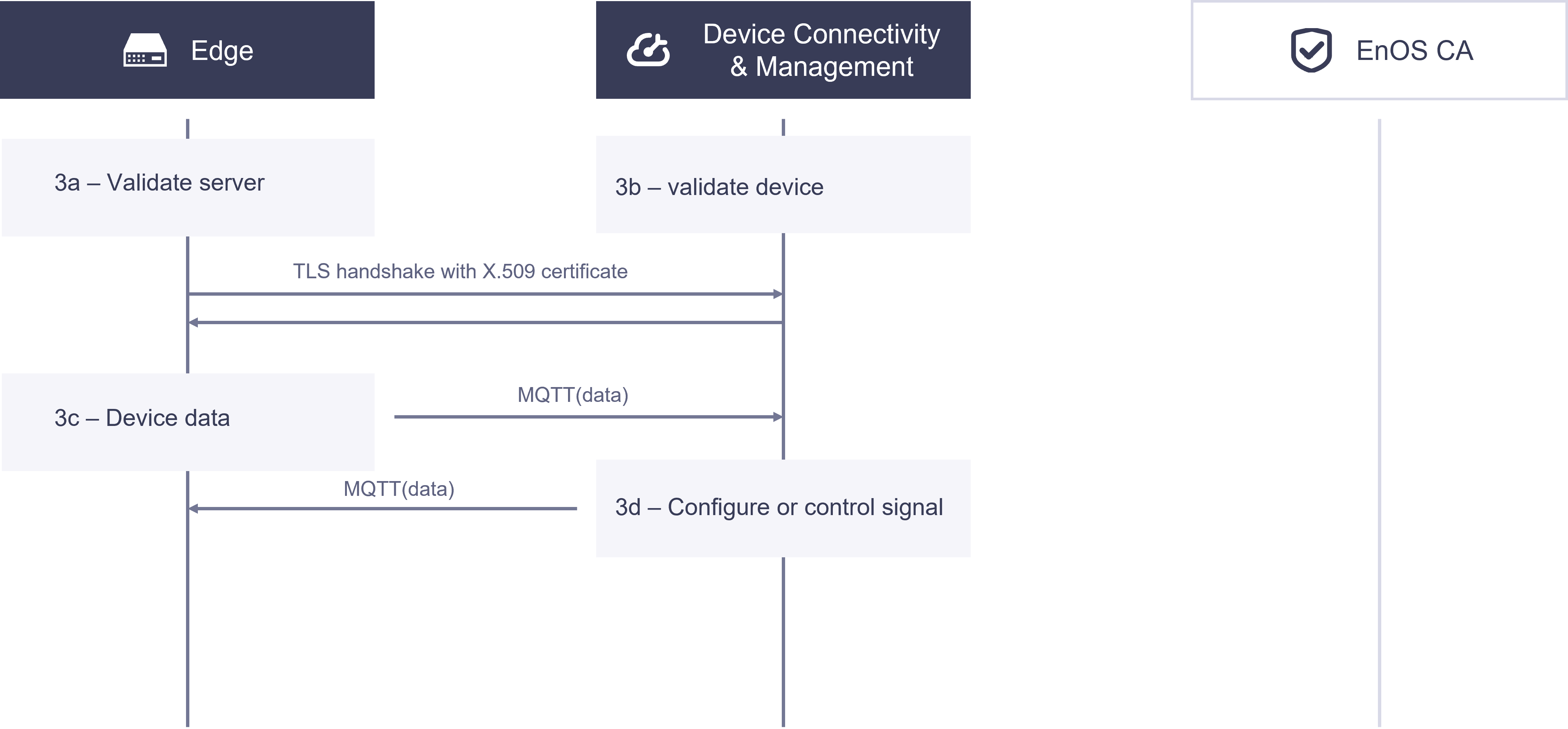
3a. EnOS Edge authenticates the certificate from Device Connectivity and Management.
3b. Device Connectivity and Management authenticates the certificate from EnOS Edge.
When the TLS handshakes in steps 1 and 2 are both successful, the TLS connection between EnOS Edge and Device Connectivity and Management is established.
3c. Within the TLS channel, EnOS Edge transmits device telemetry data using the MQTT protocol.
3d. Within the TLS channel, Device Connectivity and Management transmits configuration and control signals using the MQTT protocol.
Revoking Certificates¶
In certain cases, you may need to revoke the X.509 certificate of EnOS Edge.
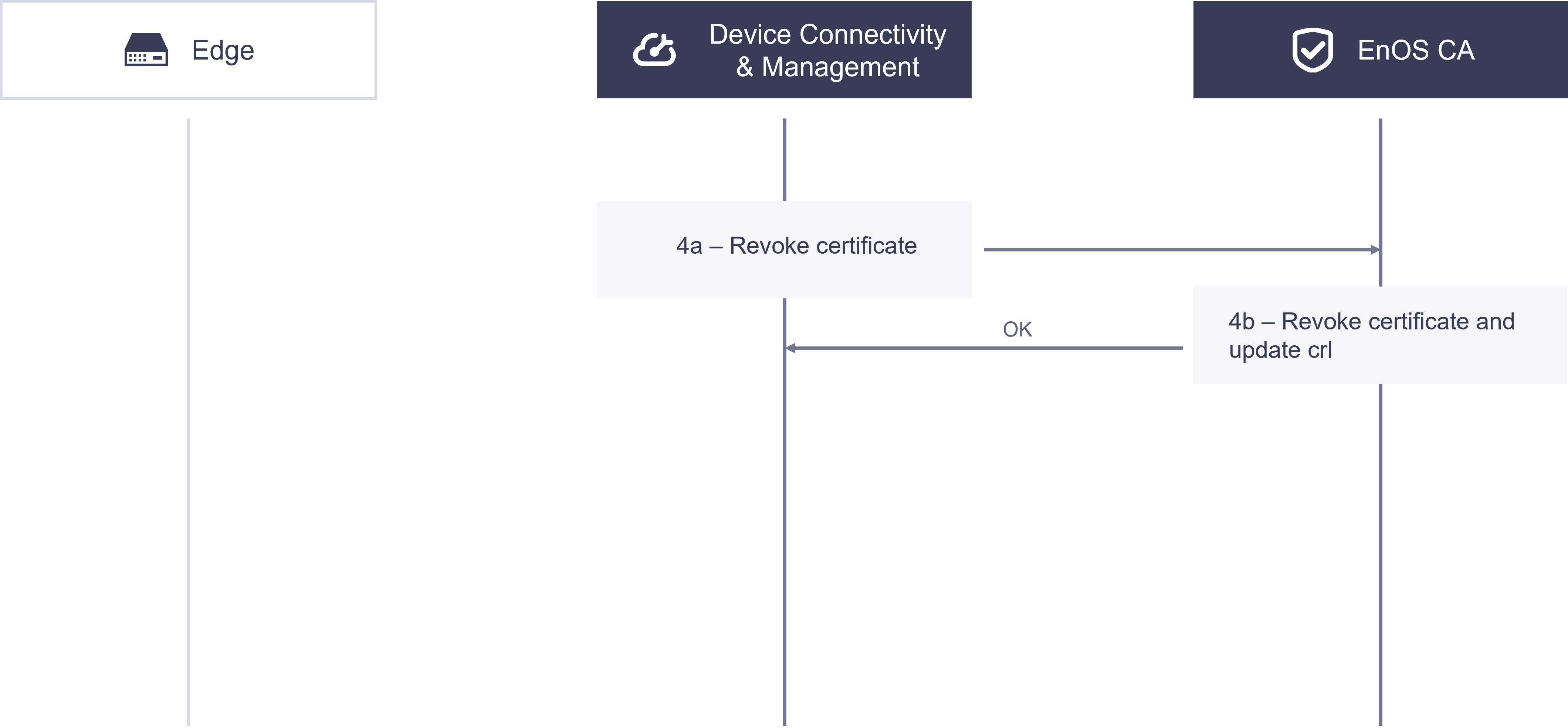
4a. Device Connectivity and Management calls the revocation API to request EnOS CA to revoke the X.509 certificate with the serial number associated with EnOS Edge.
4b. EnOS CA receives the request from Device Connectivity and Management, verifies the identity, revokes the EnOS Edge certificate, and updates the CRL.
EnOS Edge Security Best Practices¶
For certificate-based secure connections, refer to the following best practices to ensure the security of EnOS Edge:
Create a private key for EnOS Edge and store it in a secure repository, such as a TPM.
Use the TLS 1.2 protocol when communicating with Device Connectivity and Management, and verify the validity of the server certificate.
Each EnOS Edge must have a unique public-private key pair.
Keys authenticated by Device Connectivity and Management must not be used for other purposes or communicated via other protocols.
When EnOS Edge is reset, the keys must be revoked.
When your EnOS Edge runs on an operating system, ensure the operating system has security mechanisms, such as a firewall.
Ensure you have a method to update the root CA certificate and CRL.
Ensure the clock on EnOS Edge is not tampered with.